Trending
Follow us on Instagram
Reality Shrine
Entertainment
‘Lying ass tired ass b*tch’: The model Tyra Banks screamed at is seething after Netflix doc
‘We were all rooting for you’ lives rent free in my head
Jay Manuel finally shares where he and Tyra Banks stand now after America’s Next Top Model split
‘Let’s be human beings again’
Love Is Blind’s Brittany opens up on finding out Devonta had never dated a woman of colour
‘I had to process that’
On campus right now

I was jailed for five months in Japan after trying to buy k*tamine, but prison helped me heal
The former London student narrowly dodged a two-and-a-half year prison sentence

Expelled law student convicted for making hoax ‘bomb’ threat to Reading University
Muzammil Ayyaz made 700 calls threatening staff

Victims’ families hope inquiry into Nottingham attacks will finally give them closure
Grace O’Malley-Kumar’s father argued authorities ‘missed opportunities’ to prevent the attack
Internet Trends
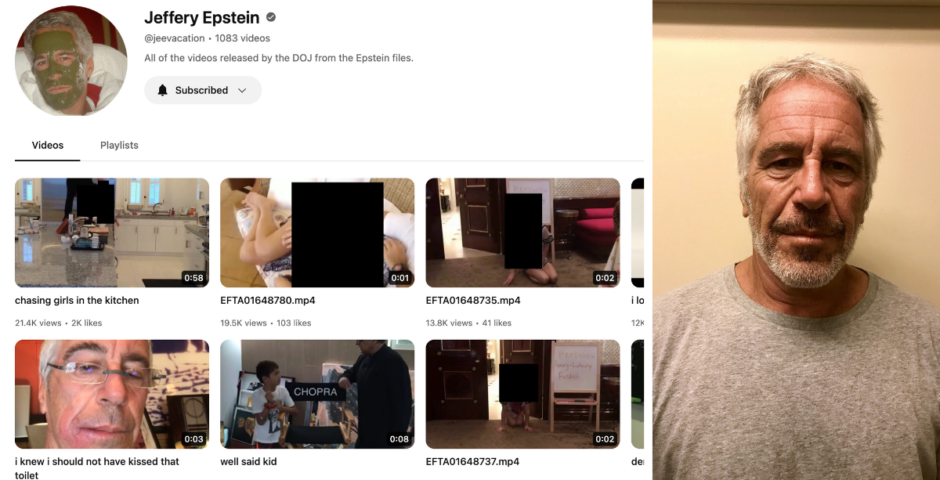
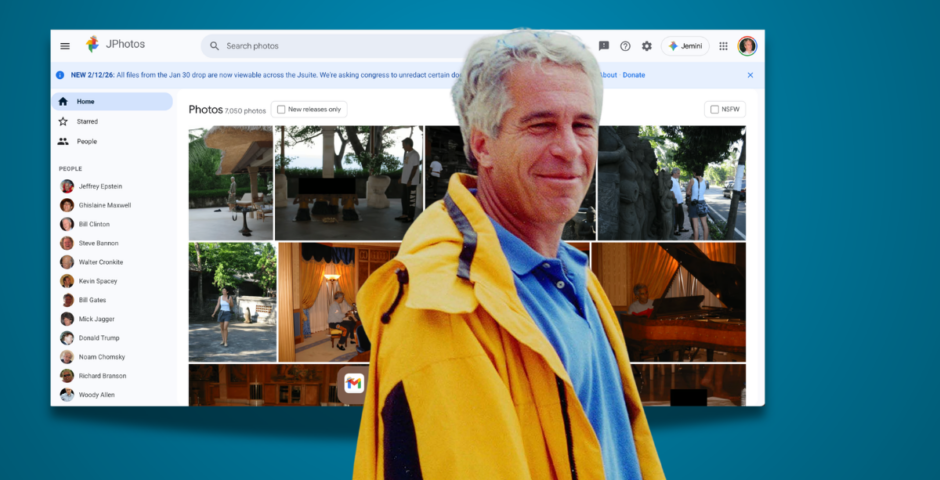
How to get JPhotos, where you can go through Epstein’s private pics like your own camera roll
There are now over 7,000 photos
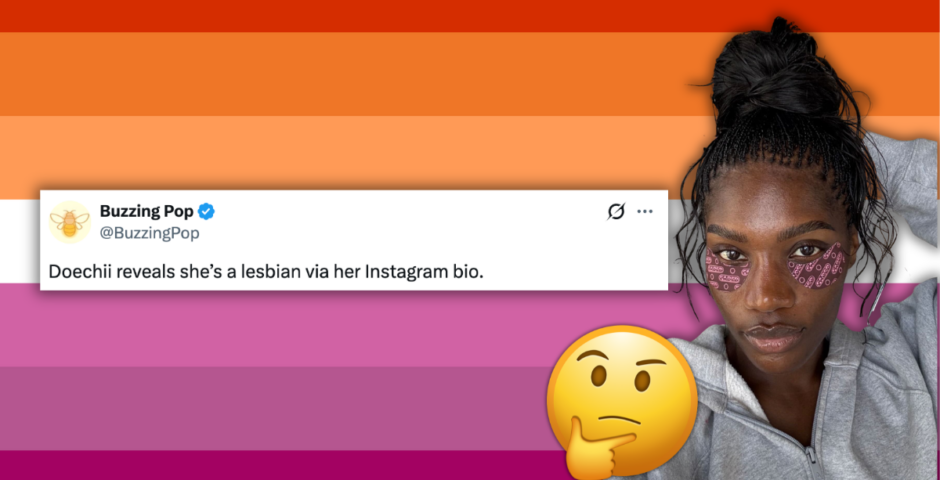
Right, here’s what ‘political lesbianism’ is, after Doechii gets backlash for coming out
There’s a huge debate around it
Amanda Seyfried reveals the backstory behind her hilariously X-rated nickname
It means something completely different to us Brits
Belle’s dad warns men what she’s *actually* like to date, after All Stars ‘hurricane’
He didn’t hold back
‘They went all night’: All the most x-rated scenes that had to be cut from Love Island
Millie and Zac’s shower kiss was actually much more explicit
Revealed: The wild thing Lucinda whispered to Belle on All Stars while they were hugging
Everyone missed the shocking comment
What Shandi Sullivan is up to now, 22 years after she was assaulted on America’s Next Top Model
Her assault was turned into a scandelous cheating storyline
Director explains what happens to Heathcliff after Wuthering Heights leaves his ending unfinished
We see what happens to Catherine, but not to him
Follow us on TikTok